Identifying Spam ASNs
I had tremendous luck building an ASN-based blacklist by expanding on honeypot IP addresses.
My honeypot using Fail2Ban
I host a simple honeypot on GCP’s free VM using Fail2Ban. It allows 3 SSH authentication attempts before banning them. I don’t ban IPs there, but on a separate machine to keep the attacks coming. Over the few months I have been running the honeypot, I have identified several hundred IP addresses.
Common patterns in the banned IPs
We can summarize all the banned IP address metadata using IPinfo’s CLI and the summarize tool. You need to install the CLI and initialize it with your token. We have the instructions for it in our GitHub repo: https://github.com/ipinfo/cli/
We will use several different IPinfo CLI commands in this tutorial. I highly recommend exploring them. The commands we will use:
grepip: Extracting IP address and CIDRs from any text.mmdb read: For reading data from the MMDB database and performing IP lookups.bulk: Batch API enrichment.Additionally, we will use common terminal commands such as
cut,sedetc.
First, let’s list out some of these banned IP addresses:
cat /var/log/fail2ban.log | ipinfo grepip -o | ipinfo summarize
Output
Summary
- Total 377
- Unique 46
- Anycast 0
- Bogon 0
- Mobile 0
- VPN 29
- Proxy 0
- Hosting 281
- Tor 0
- Relay 0
Top ASNs
- AS132203 Tencent Building, Kejizhongyi Avenue 94 (24.9%)
- AS14061 DigitalOcean, LLC 44 (11.7%)
- AS45090 Shenzhen Tencent Computer Systems Company Limited 34 (9.0%)
- AS135377 UCLOUD INFORMATION TECHNOLOGY (HK) LIMITED 24 (6.4%)
- AS63949 Akamai Connected Cloud 21 (5.6%)
Top Usage Types
- Hosting 251 (66.6%)
- ISP 77 (20.4%)
- Education 33 (8.8%)
- Business 14 (3.7%)
Top Routes
- 43.153.0.0/18 (AS132203) 25 (6.6%)
- 190.188.0.0/15 (AS7303) 17 (4.5%)
- 205.185.112.0/20 (AS53667) 17 (4.5%)
- 103.170.86.0/23 (AS141286) 16 (4.2%)
- 170.64.224.0/20 (AS14061) 16 (4.2%)
Top Countries
- United States 73 (19.4%)
- Singapore 70 (18.6%)
- China 69 (18.3%)
- India 32 (8.5%)
- Australia 24 (6.4%)
Top Cities
- Singapore, Singapore, SG 70 (18.6%)
- Beijing, Beijing, CN 33 (8.8%)
- Santa Clara, California, US 25 (6.6%)
- Los Angeles, California, US 24 (6.4%)
- Sydney, New South Wales, AU 24 (6.4%)
Top Regions
- Singapore, SG 70 (18.6%)
- California, US 50 (13.3%)
- Beijing, CN 33 (8.8%)
- New South Wales, AU 24 (6.4%)
- Hesse, DE 20 (5.3%)
Top Privacy Services
- VPN99 12 (3.2%)
- TunnelBear 12 (3.2%)
- foxyproxy 5 (1.3%)
Top Domains
- prod-infinitum.com.mx 18 (4.8%)
- prima.net.ar 17 (4.5%)
- 172-235-28-140.ip.linodeusercontent.com 16 (4.2%)
- mosawn.com 12 (3.2%)
Based on the IPinfo summary information of the banned IP addresses, it is interesting that a country-based blocklist would not be effective, as the US and SG, common non-threat countries, are the origin of one-third of these failed SSH attempts.
However, in the ASN section, we can see that Tencent (AS132203, AS45090) and Digital Ocean (AS14061) IPs are being used in 40% of the attacks. So, by looking at the spam IPs, we can first build an ASN-based blocklist.
Extracting the ASNs and ASN-owned ranges using IPinfo’s free IP database
For this step, we will use the free IP to ASN database. You can use our free IP to Country ASN database, as well as it provides country-level location information. But as we do not need it now, our IP to ASN database is adequate for this section.
You need to download both the CSV and MMDB versions of the file. We need the MMDB version for the IP to ASN lookup and the CSV version for the ASN to IP range lookup.
Download them using the following commands on the CLI:
ipinfo download asn -f csv; ipinfo download asn -f mmdb
This will download two files:
asn.csv: The CSV format of the IP to ASN databaseasn.mmdb: The MMDB format of the IP to ASN database
After downloading the IP to ASN database, we will store our banned IPs in a file called "banned_ips.txt.
cat /var/log/fail2ban.log | ipinfo grepip -o | sort -u > banned_ips.txt
banned_ips.txt
101.32.141.81
103.160.154.23
103.170.86.94
110.42.183.85
111.229.10.88
[...]
Now, we can get the ASNs of these banned IP addresses using the MMDB version of the IP to ASN database (asn.mmdb).
(ipinfo mmdb read banned_ips.txt asn.mmdb -f csv) | tail -n +2 | cut -d ',' -f2 | sort -u > asns.txt
asns.txt
AS132203
AS135377
AS138077
AS14061
AS141286
[...]
Although not all of these ASNs actively engage in suspicious activity, they are hosting IP addresses linked to attacks on my server.
From there, we can build the blocklist by listing all the ranges these ASNs own. For this step, we will use the Free IP to ASN database in CSV format (asn.csv).
((head -1 asn.csv;grep -f asns.txt asn.csv | ipinfo range2cidr | cut -d',' -f1) | tail -n +2) > asn_ranges.txt
1.12.0.0/14
1.48.0.0/18
1.48.128.0/18
1.48.224.0/19
1.49.0.0/18
[...]
Exploring StopForumSpam and extracting the ASN
StopForumSpam is a great platform and open-source initiative that helps forums prevent spam. Users can submit forum and blog spam IP addresses to the platform. SFS curates a large list of IP addresses from this crowdsourced information and makes it available via API and data downloads.
You can explore their data downloads section here: https://www.stopforumspam.com/downloads
We are going to use their toxic_ip_cidr.txt list.
103.81.182.0/24
109.200.1.0/24
109.200.2.0/23
[...]
Because these are CIDRs and we just need the ASNs, we do not need to go through each IP address of the CIDR. We can just use the network address.
cat sfs_cidr.txt | cut -d '/' -f1 > sfs_ips.txt
103.81.182.0
109.200.1.0
109.200.2.0
109.200.4.0
109.200.8.0
[...]
From there, we can get the ASNs that own these ranges using the asn.mmdb database:
((ipinfo mmdb read sfs_ips.txt asn.mmdb -f csv) | tail -n +2 | cut -d',' -f2 | sort -u) > asns.txt
asns.txt
AS12876
AS15895
AS201776
AS206728
AS206791
[...]
Then we get the range from the asn.csv database:
((head -1 asn.csv;grep -f sfs_asns.txt asn.csv | ipinfo range2cidr | cut -d ',' -f1) | tail -n +3) > sfs_asn_ranges.txt
sfs_asn_ranges.txt
1.0.0.0/24
1.0.4.0/22
1.0.16.0/24
1.0.32.0/24
1.0.64.0/18
1.0.128.0/17
1.1.1.0/24
1.1.8.0/24
1.1.64.0/19
Parameters for identifying spam ASN.
The Twitter thread that sparked the discussion was started by Jesse from Bento.
I basically want to grab a list of trash ASNs (like this Moldovan dc which no Bento customer would be making requests from)
That is a good point, and for this, they can use the free IP to Country ASN database.
Whenever you find a spam IP address, look it up in the IP to Country ASN database. Then, you can list the suspicious ASNs using a combination of country and ASN. You can modify the code we have so far. You can use grep or an SQL database.
ipinfo mmdb read sfs_ips.txt country_asn.mmdb -f csv
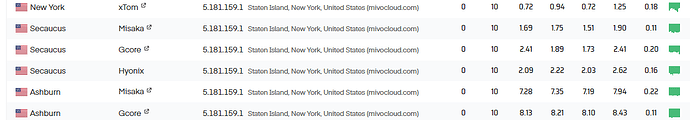
Jesse mentioned “5.181.159.5” and said that the IP address is from MivoCloud (AS39798) and assumed is based in Moldova.
First, 5.181.159.5 is not located in Moldova; it is in New York, according to our data. Even though the IP address in question is not pingable, if we use our Pingable IP tool and ping a few nearby pingable IPs on its /24 range, we can see that all of them have the lowest latency from New York servers. We have high confidence that the IP address is located in New York.
So, the first part is using accurate data. ![]()
Then comes the additional attributes, you can use SFS IP list or your spam list. What you need to do is create dynamic ASN lists using country and ASN. Moreover, if you explore some of our other paid databases, you can get ASN type information, privacy detection information, company information etc. In my experience with exploring Click Farm IPs, I have found evidence (at least in the case of South Asia), that Click Farms tend to use Carrier IPs.
Depending on your use case, we highly recommend fine-tuning the mechanism that considers the ASNs suspicious.
Like the case with 5.181.159.5, the IP address belongs to a data center in New York, which could have been considered a “low threat” because it is a US IP address. So, it all comes down to how you accurately parameterize these spam ASN based on IP country, ASN and other IP metadata. Go through your log and see what we say about the IP addresses, and based on the frequency of spam IPs and your intuition, parameterize the attributes that could deem an ASN to be spam.
Using our free IP database is quite easy, and creating a suspicious ASN dataset (and its ranges) is easy as well. If you need help, we are always here to help! In fact, please feel free to send me spam IPs, and I would be happy to take a look!